20+ firewall diagram examples
On the diagram below there is a GRE tunnel between Switch1 again this is usually an ASR1000 or 7600 etc and remote Switch2. NetworkPolicy features and examples.

Standard Firewall Example Connection To Intranet 3 Distributed Download Scientific Diagram
Random freeze of the firewall.

. Linux file permissions involve read write and execute permissions. We started an EC2 instance in the public subnet of a VPC and then we set up the security group firewall to enable access from anywhere using SSH and TCP 5601 Kibana. Fallback Values In CSS Variables.
A data connection is initiated on port number 20. Its an essential command that pretty much every user will find the need to utilize at least every once in a while. Using NetworkPolicy is a way to enforce network isolation of selected pods.
Mommy I found it. By default the network traffic from and to K8s pods is not restricted in any way. -- 15 Practical Linux Find.
Vi and Vim Macro Tutorial. Based on the command line you are able to identify where you are in the IOS XR command prompt. It uses examples from the preceding diagram.
How To Record and Play. The following diagram shows a tailored Azure landing zone hierarchy. All four values are predictable considering the inheritance logic in the above diagram.
HTTP and SMTP are such examples. The OVS software based solution is CPU intensive affecting system performance and preventing fully utilizing available bandwidth. This document provides examples of basic Network Address Translation NAT and Port Address Translation PAT configurations on the Cisco Secure Adaptive Security Appliance ASA Firewall.
Get a Grip on the Grep. This is a guide to Number Systems. 15 Examples To Master Linux Command Line History.
Consider the following points when you think about tailoring your implementation of Azure landing zone archetypes in the hierarchy. 1952 Chevrolet 31003604 relay diagram. This Azure Diagram template is a good example of what an Azure architecture diagram looks like.
Ground for the relay is thru the mount to the firewall and ground to the horn is thru its mount or a separate ground wire. The main fuse box also known as the Power Distribution Module or PDM is located under the hood on the left front fender just ahead of the bulkhead moduleThe fuses in the main fuse box are paddle type mini fusesThe battery power fuses located next to the batteries are screw-in mega fuses. You can also go through our other suggested articles to learn more Introduction to jQuery toggle jQuery empty Examples How to Use jQuery insertAfter Method.
Tailoring the hierarchy isnt mandatory. These permissions can be assigned to the file or directory by its owner a group of users or other users users that are. Top 10 Open Source Bug Tracking System.
2016-01-20 Elasticsearch will automatically map the payload field as a date field. Here we discuss a Brief Overview of Number Systems and its different types along with their examples. I have been running opnsense 1879 for a couple of months now.
This document also provides simplified network diagrams. 0646d Freightliner Fld 120 Wiring Diagram Digital Resources from. The GRE tunnel is established between IP address 172161010 on switch1 and 10101010 on switch2.
This is of course a simplified diagram for the sake of illustration. 15 Awesome Cron Job Examples. 10 4 Ventilation 8 and safe load feeders 3RA71 A.
Within the scanning window you may see traffic through various ports such as 110 pop3 80 web and a few others. To further get an idea of what a professional diagram should look like here are some Azure diagram examples that you can check out. 15 Practical Grep Command Examples.
For this reason they are said to send their control information in-band. Fallback values are the second argument used in the var function which denotes the substitution of a CSS variable. FTP sends the control information out-of-band as it uses a separate control connection.
Consult the ASA documentation for your ASA software version for more detailed information. Kool Firewall has built-in. Kool Firewall is firewall security software designed to monitor the traffic into and out of your system.
We want to send traffic from fa01 on Switch1 to fa05 on Switch2. In this article. The chmod command in Linux is used to manage file permissions.
Some protocols send their request and response header lines and the data in the same TCP connection. The server will see that the DHCP request came from source subnet 1921681024 and will therefore assign an appropriate IP address from a configured IP pool scope within the. By configuring an ip helper-address 1010101 under interface Fe00 of Router A we tell the router to turn the DHCP broadcast into a DHCP unicast and send it to destination DHCP server 1010101.
In this template the networking system of a certain organization is depicted. In the following diagram I hope to give you the idea of configuration in a task group and configuration as root-system users or Admin. When pressed it completes the circuit to ground pulls the plunger down on the relay and makes contact with the H terminal which supplies power to the horns.

Networking Security Foundations Google Cloud

What Are Stateful And Stateless Firewalls

Networking Pills
Why Don T More Governments Use Openbsd Org As A Router Firewall Etc Solution To Replace Expensive Commercial Cisco Etc It Is Free And Very Secure Quora

Userguide Nethserver And Proxmox Nethserver Wiki

Firewall Dmz Configuration In 2022 Private Network Network Architecture Segmentation

Tcp State Diagram Of Carrier A S Firewall Download Scientific Diagram

Networking For Secure Intra Cloud Access Reference Architectures Cloud Architecture Center Google Cloud

Azure Fundamentals Day 3 Training General Security And Features

Example Of Ips On A Network Firewalls And Ips Download Scientific Diagram

A Medium Size Network With Dmz Download Scientific Diagram
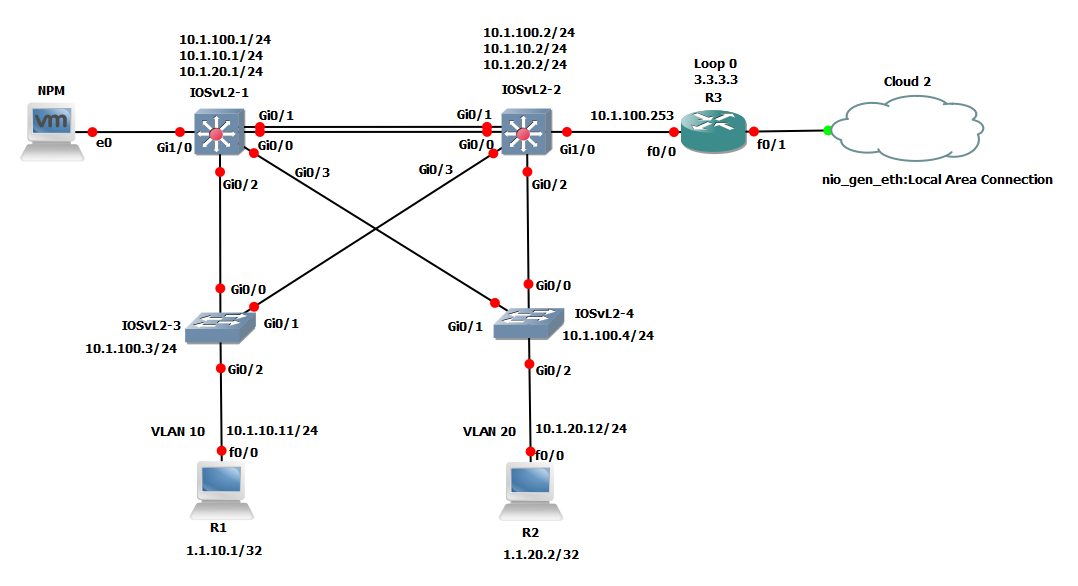
Getting Started With Gns3 Gns3 Documentation
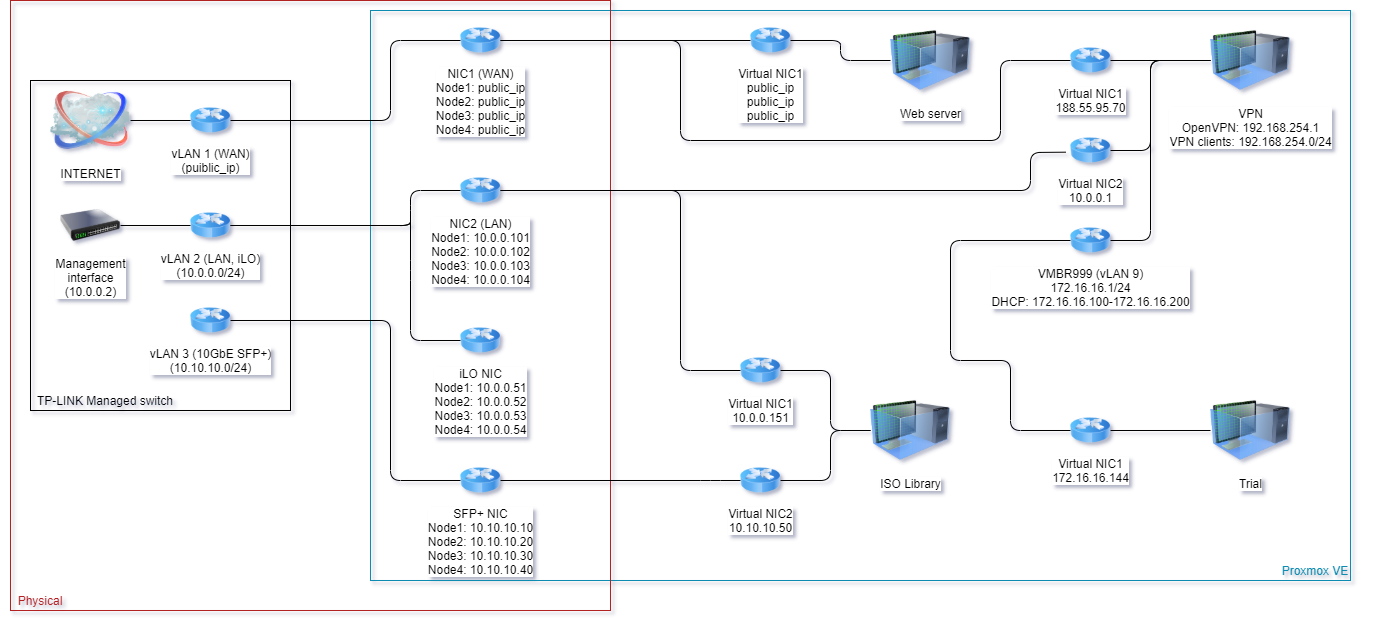
Public Ip Behind Firewall 21 By Andy Wismer Support Nethserver Community

1 Hardware Firewall Network Diagram Download Scientific Diagram

Standard Firewall Example Connection To Intranet 3 Distributed Download Scientific Diagram
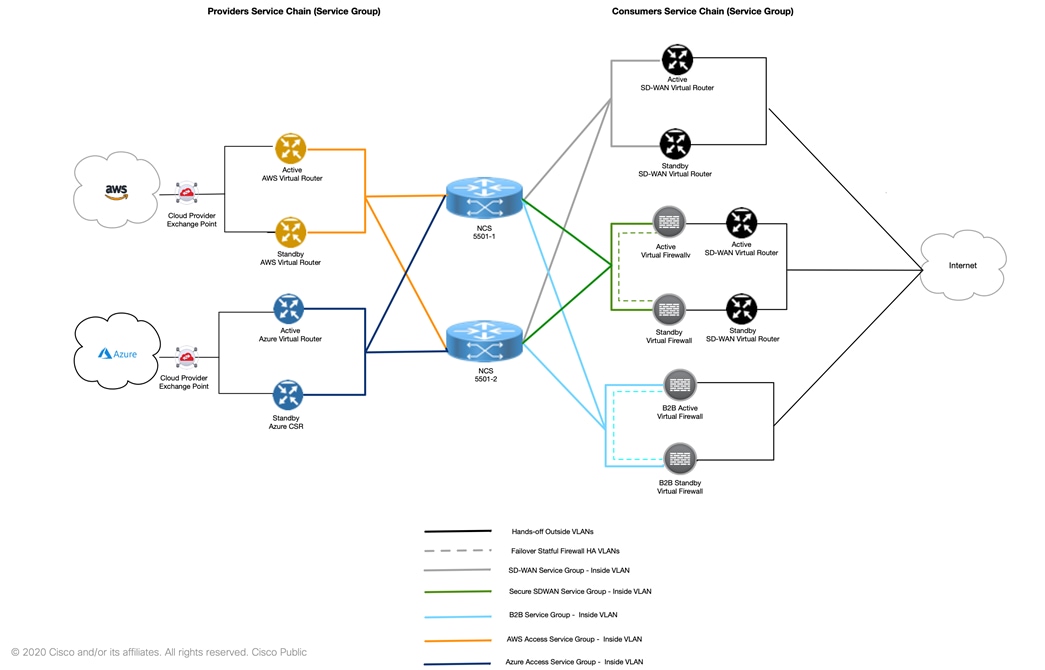
Solutions Cisco Secure Access Services Edge Sase Deployment Case Study Cisco

Example Network Firewall Is Intended To Protect Network From Internet Download Scientific Diagram